08 January 2019
With criminals increasingly targeting mobile users and fraud on the rise, the issue of security is never far from the headlines.
So how can operators safeguard their networks and stay one step ahead of the hackers? RAHIEL NASIR asks the experts.
Mobile networks are coming under increasing attack from fraudsters, hackers and cyber criminals.

For example, South Africa’s position as one of the continent’s fastest-growing telecoms markets makes it an increasingly attractive target for cyber criminals.
In a study published earlier this year in March, threat intelligence specialist Anomali cited a number of reports about cyber attacks on South African service providers.
These included: Telkom being hit by WannaCry ransomware in 2016; a flaw in Vodacom’s portal that allowed any subscriber to access high-level account summary information linked to any phone number; customer records becoming accessible following a flaw that was discovered in Cell C’s portal; and sensitive information that was found accessible in MTN’s e-billing portal.
The latter, along with affiliated service providers, also suffered a service outage due to a DDoS attack in 2013.
Anomali also quoted the global Threat Impact index from security specialist Check Point.
South Africa was ranked 21 in the global list of countries and was placed ninth overall in Africa, but is by no means the country that is most at risk on the continent.
Zambia, Nigeria, Uganda and Malawi all fared worse.
Whilst cyber crime in general is a global issue that can impact anyone and any body, from individual consumers and organisations to governments and states, mobile operators face the additional scourge of revenue leakages through, for example, the fraudulent use of SIM boxes, particularly in Africa.
Biren Sasmal, CEO of Ghana-based revenue assurance specialist Subah, says:
“The reality is that Africa has been hit by several telecom frauds. SIM box fraud, also known as the interconnect bypass fraud, is one of the major ones affecting the market. The impact is huge in terms of the loss in revenues to telcos and taxes to the government. It is estimated that Africa loses more than USD200m every year to interconnection frauds. I have seen more than 80 per cent of African operators facing SIM box fraud.”
Sasmal says a major misconception is that SIM box fraud happens in countries with very high termination rate.
“The moneymaking opportunity for the fraudsters is the differential between the international termination rate and the local termination rate. So even in countries where that is only a few cents, there’s still enough margin for fraudsters to make money.”
UK-based telecoms revenue assurance specialist Revector has been active on the continent and tracking down SIM boxes since 2008.
Its founder and CEO Andy Gent explains that the company recently worked with a major low-cost carrier in one West African country that had been targeted by fraudsters and seen an 80 per cent decline in business.
“Three months later, Revector [was able to] return USD500,000 revenues per month of increased inbound traffic – USD22,600 per business day – as the fraudster sending the traffic could no longer keep up with the ‘cut off’ SIM box numbers it needed to replace. The SIM box route into the country then failed and got switched off by the low-cost carrier.”
Nonetheless, SIM box fraudsters continue to thrive in Africa.
“Each year, I want to believe the MNOs would have invested the effort and addressed this as well as the new and highly costly OTT bypass issue,” says Gent. “This is not the case: changing rates from promotional tariffs and cross-border plans continue to encourage international bypass. The reality is that the marketing teams should work much more closely with the fraud teams across the continent.”
The i3forum is a not-for-profit industry body that brings together the international carrier ecosystem to enable and accelerate transformation.
It believes operators in Africa have been traditionally exposed to higher levels of fraud incidents compared to other regions – as well as SIM boxing, it says subscription, international revenue share fraud (IRSF), and partner channel frauds are some of the most prevalent.
Katia González, chair of the forum’s fraud group and also head of fraud prevention at BICS, says:
“While operators have been investing a lot in SIM box protection, IRSF issues are starting to get more attention. ‘Wangiri’, a form of IRSF, has reached an epidemic level specifically in Africa but it’s also a fast-growing fraud scheme around the world.”
‘Wangiri’ originated in Japan and is said to mean ‘one ring and drop’. Those behind the scam literally do just that – they call a mobile or fixed line number, let it ring once, and then drop the call. Unsuspecting mobile users see a missed call from an international number that they don’t recognise, and the fraudsters hope that their expensive, premium rate per minute international numbers will be called back so that they can profit. González says targeting Wangiri is one of the key focus areas for the i3Forum’s Fight Against Fraud workgroup.
Sasmal points out that signalling security and the design of signalling protocols for next generation networks also needs to take centre stage and is crucial for the success of the industry and future networks.

“If each MNO or carrier goes it alone and tries to deploy their own solutions, we will never be successful.”
This was highlighted earlier this year when AdaptiveMobile Security announced it had detected what it described as “increasingly sophisticated” attacks via the next-generation of the Diameter signalling protocols being used for 4G.
To acquire its insights, the company said it analysed international traffic that used Diameter from 10 mobile networks worldwide.
It looked at traffic travelling to and from more than 80 countries across five continents and claimed to have detected a range of malicious activity, from simple to complex, affecting both mobile subscribers and mobile networks.
Speaking at the time, AdaptiveMobile’s chief intelligence officer Cathal Mc Daid said that up until now, Diameter vulnerabilities were thought to be theoretical.
“This new research clearly demonstrates that they are actually being exploited in the real world, meaning the risk is real and must be addressed. Most importantly, carriers need to understand what is being detected and cannot rely on simple categorisation or rules to decipher what is malicious activity and what is not.”
Mc Daid went on to warn that while the threat is now proven, malicious traffic will remain hidden “amongst the noise” without an added and critical layer of intelligence.
“As Diameter use widens and SS7 security improves we expect rogue actors to exploit Diameter more and more.”
What MNOs should look for
Having said that, the MNO still remains the gatekeeper in all this – to reiterate González’s point above no one is going to protect the operators’ networks and infrastructure on their behalf.
So when choosing an assurance solution to protect against revenue leakages, what do the cellcos need to look for?
“There are many types of solutions and not one fits all needs,”says Gent. “My personal view as an ex-CEO of a major operator is to go for a proven solution from a reliable vendor and not the latest sales pitch. Test the vendors, and get them in to analyse your network for risks. Every single fraud and revenue assurance service provider should be able to prove a return on your investment.”
According to Subah’s Sasmal, revenue leakage generally occurs in the organisational process and/or the technology side of business. “It can come anywhere in the revenue cycle, from sales to network configuration and rating and billing."
“The areas most vulnerable to leakage and fraud are the revenue streams with the largest volume of payments including pre-paid, roaming and post-paid plans. Many revenue leaks occur because organisations don’t have integrated, real-time access to service or contract data, and they use manual analysis rather than automated processes.”
This latter point is crucial for Subex which believes AI and predictive analytics represent the future.
Maheshwari claims the company is committed to ushering in this future where all of its customers, including MNOs, will be able to predict with certainty the consequences of every action they take, and therefore predict and avoid every risk and every threat.
Maheshwari also advises MNOs to avoid the ‘old ways’ of choosing and using OSS/BSS vendors.
“While in traditional thinking, efficiency demands singularity of approach, nature teaches us singularity is a sure way to extinction. Similarly, in fraud and security, the one trick pony will be found out sooner than later. So ask if the vendor has a multi-pronged, multi-dimensional approach to solving fraud and security challenges.”
Like Subex, Amdocs also says that machine learning- and AI-based methodologies should be part of the solution, and that a different approach is now needed when it comes to selecting a platform.
“Service providers are becoming digital service providers. Many of the traditional revenue assurance methodologies – rule and statistics based on knowledge of human experts which worked well in past decades – are not enough to support the new digital ecosystems.”
González echoes this view when she says that operators are working in a mode of “incident-induced learning” with a silo view on fraud prevention.
Her recommendation is to look at a solution that provides fraud intelligence around the world, seamlessly and efficiently.
“Detection mode is highly unreliable and always introduces delays in fraud prevention. MNOs should look for more proactive and real-time ways to prevent fraudulent attacks from happening.
“Most incidents of fraud actually occur during non-business hours. That’s why 24x7 fraud coverage is an absolute must. New data feeds and technologies such as Big Data and signalling analysis should be focus areas of investment for operators so they can go to the next level in fraud prevention.”
More tech, more opportunities for the bad guys?
From a security perspective, are things only set to get worse for MNOs as they progress from 3G to 4G and beyond, and also move out to the edge and connect objects in the IoT?
“As African mobile carriers adopt the latest technologies, we firmly believe that new cyber fraud challenges will emerge,” says Michal Sever, product marketing manager for Amdocs’ Revenue Guard.
“This will lead to verification and customer authentication in digital self-service channels (i.e. digital transactions through mobile). Applications through operators and/or web portals will ramp up. In addition, increasing internet speeds and bandwidth will enable operators to offer advanced IoT applications and services, hence new security challenge are expected to emerge in this space as well.”

“Many revenue leaks occur because organisations don’t have integrated, real-time access to service or contract data, and they use manual analysis rather than automated processes.”
González is likely to support this view when she says that the mobile ecosystem is continually growing, and when moving from end users to end points the opportunities for fraudsters grows.
“Without proper focus on security and investment, the hacking of IoT devices may become the main method of security threats to operator networks.
“Organisations and consumers have a growing number of connected devices that hackers are targeting. This challenge will only continue to grow as the number of smart devices we use multiplies.”
But Revector’s Gent is not so pessimistic:
“4G is building in new security; IoT will be a challenge but if the MNOs build a complete security team and rise to the challenges they can protect themselves.”
If there was one thing that many of the industry experts we spoke to agreed upon, it was the view that mobile security is not just an MNO problem.
“We are at a critical time for the entire telecoms ecosystem. Our businesses are diversifying, and we have to work together to ensure that services are both secure and profitable,” says González. “The industry as a whole has to collaborate and work together to create secure environments that are not easy targets for fraudsters. If each MNO or carrier goes it alone and tries to deploy their own solutions, we will never be successful. The whole ecosystem is more interconnected than it has ever been and we have to view the fight against fraud in the same way.”
She goes on to state that while operators are responsible for protecting their networks and infrastructure, support from governments and regulators can ensure there’s a set process that can be followed.
“By enforcing these policies, they can help advocate and protect consumers from fraudulent attacks. Having this support will promote the sharing of information between operators and wholesale carriers in a coordinated way.
“Ultimately, it’s up to the carriers to work together with whoever will stand up and collaborate to fight fraud. Across the entire ecosystem, which includes governments and regulators, we have to work together to limit the damage being done by fraud. A fraud-free environment will enforce trust on the telecom industry and benefit everyone related to it directly or indirectly.”
The Internet Society also highlights the issue of trust which it sees as key to advancing Africa’s digital economy.
At the Africa Internet Summit held in Senegal last May, the society unveiled The Personal Data Protection Guidelines for Africa.

“IoT will be a challenge but if the MNOs build a complete security team and rise to the challenges they can protect themselves.”
They have been jointly developed by the Internet Society and the African Union Commission to facilitate the implementation of the AU’s Convention on Cyber Security and Data Protection (known as the ‘Malabo Convention’), adopted in 2014.
Speaking at the time, Dawit Bekele, the Internet Society’s African regional bureau director, said:
‘The lack of appropriate protection for personal data can have a profound impact not just on individuals but also on society at large, to the point of endangering democratic systems. These guidelines explain how people can take a more active role in the protection of their own data as well as the role that other stakeholders, including governments and legislators, have in ensuring the proper use of data.”
The guidelines urge all AU member states to firstly recognise privacy as a foundation for trust in the digital environment, and secondly, prioritise the sustainable and responsible use of personal data in the digital economy.
In addition, there are recommendations for citizens such as being aware of the risks and benefits of the digital economy or their online activities; knowing how to exercise their rights under privacy and personal data protection laws; and developing the capabilities to protect their interests online.

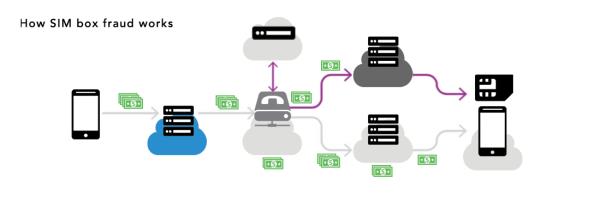
An illegal SIM box in Congo. SIM box fraud is particularly rampant in countries with high numbers of incoming international traffic where SIM availability is loosely controlled and law enforcement is lacking. The fraudsters mainly use pre-paid SIMs where the ownership and address is hard to detect. There are many variations of SIM box fraud and methods of detecting them therefore also vary.
So the entire issue of mobile and digital security does not just begin and end with the mobile network or other service provider. As stated before, it has an impact on all of us, and so even individual consumers need to know their responsibilities are when it comes to the safe use of digital services.
“Africa is still largely a voice-centric market where MNOs and carriers are being challenged by voice fraud,” says González."Our recommendation to operators across the continent is to get involved in the fight against fraud, share information and follow the ITW Global Leaders’ Forum’s and i3forum’s Code of Conduct. The ultimate purpose of this code is to prevent fraudsters profiting from criminal activity and bring a lasting impact on the carrier ecosystem. It requires a joint effort and if we are all on the same page across the globe, then we can make a coordinated effort to fight fraud.”






